Projects
1. Busybee
Year: 2021 - 2022
Website: www.busybee.se
In early 2021 myself and a few friends co-founded Busybee. Busybee provided customers with in-depth data & analytics about people flow in their venues. You could visit our web app to see how busy our customer’s venues were as well as predictions on future traffic. More importantly, customers could log into a admin panel and see in-depth information on occupancy levels in their buildings. Like many start-ups and small scale projects, my role in Busybee was a bit of everything. As an engineer, my primary contributions were building the entire backend infrastructure for Busybee alongside my two colleagues. This wasn’t just limited to the services processing and analysing the occupancy data, but the graft of actually installing and setting up the physical sensors in our partner’s venues.
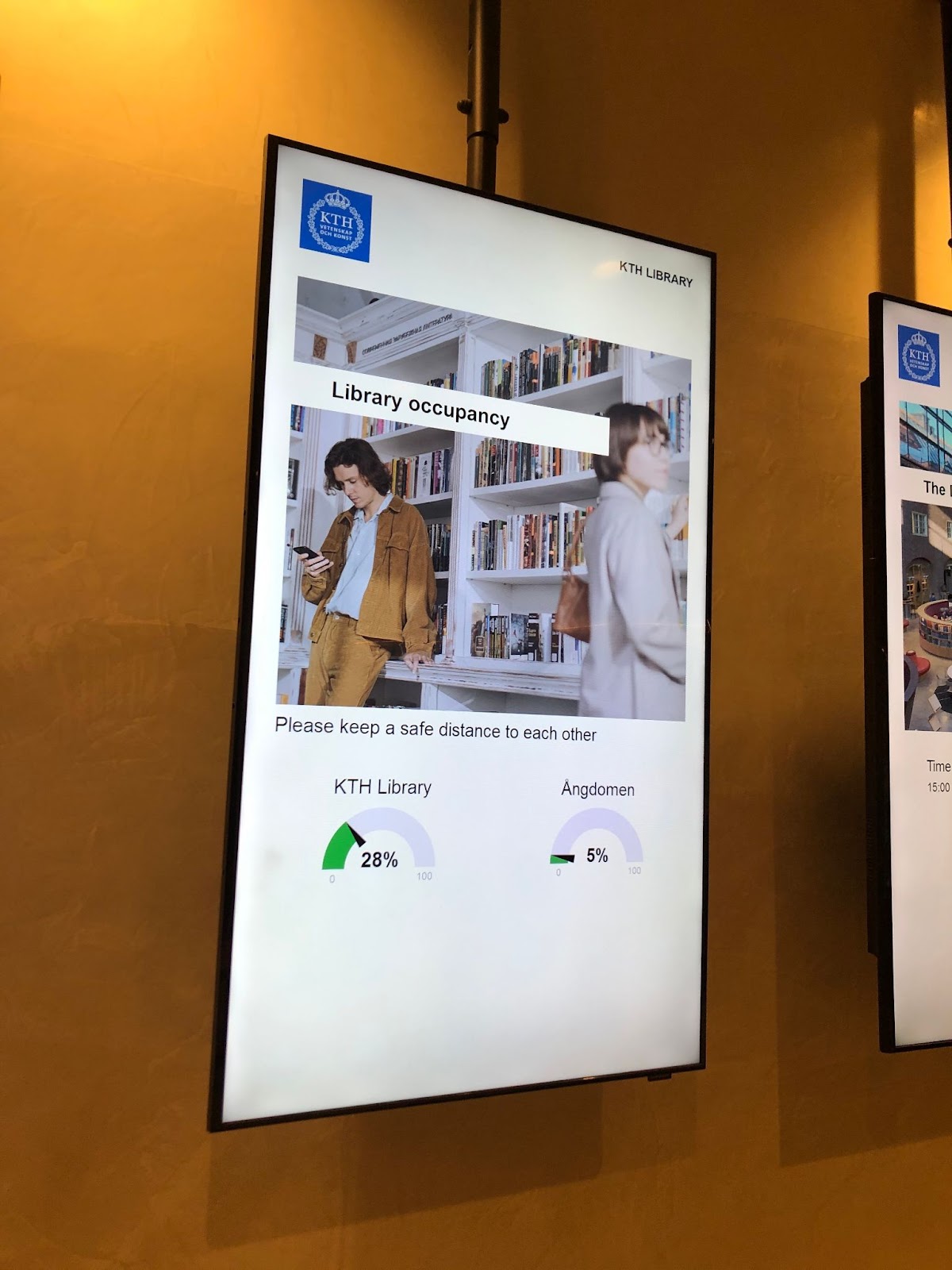
We initially developed Busybee at KTH’s library. There we installed sensors to detect people flow and then published the occupancy levels both online and to TV screens in the entrance to the building. Since this was at the height of the Covid pandemic, we developed several features to assist administrators at the library comply with strict Covid-19 regulations. Such as SMS alerts to staff once recommended occupancy limits were reached. Busybee grew and we onboarded a couple more customers.
Below you can see our KTH Innovation demo day poster to get a better idea of the project.

2. Hacking lab
Year: 2021 - 2022

During my time as a research engineer at KTH I was put in charge of a hacking lab. This lab was used as a space for penetration testing all types of hardware and electronic equipment. Examples include: airport X-ray machines, PLC’s used in residential buildings, computers controlling power grids, and many more! My role in the lab was to ensure that all the equipment was set up properly and that researchers and students could hack easily. Some of the things I worked on in the lab:
- Website containing resources on hacking (described above)
- A VPN that allowed remote access to the lab’s network
- Setting up physical servers in the room to be used for pen testing
- Setting up local networks for Wi-Fi sniffing
- Purchasing and setting up equipment for Bluetooth sniffing
3. Cyber security website
Year: 2019-2022
Website: www.nse.digital
Source code: Github repo
During my time as a cyber security research engineer at KTH I created a public documentation website to be used by students and researchers at the university. I created the site a few years ago , in 2019, and it is still regularly updated today and has been a source of information for hundreds of students. I wrote many of the guides that are still up there on the site. There are a group of regular contributors to the site including professors, PhD students and other researchers.
The motivation for creating the site was to allow students and researchers to share information with each other. I realised while working at the university that many students coming in to conduct penetration testing research were going through the same repeated steps. Products might vary wildly in usage, but if they used BLE or 4G technologies your surface of attack would look very similar. Therefore having a centralised website for hacking that anyone could contribute to was a great (and importantly: self sustaining) solution.
4. Penetration testing an electric scooter
Year: 2019
Website: KTH Thesis Portal
News article: SVT
As part of my Bachelor’s thesis I hacked a popular electric scooter. The scooter uses Bluetooth Low Energy to communicate to a user’s mobile phone, where they can control the scooter and upload firmware updates. We managed to reproduce attacks which would allow an unauthorised attacker the ability to lock and control someone else’s scooter. I was interviewed by Swedish national news about the scooter hack and our published thesis has several thousand downloads and a handful of citations. You can check out my Bachelor’s thesis here.